If you read a lot of news, chances are the task of securing your data from a threat looks rather daunting. Hardly a day goes by without some major hack reaching the front page. Data breaches at HBO, Parity Ethereum, Bupa, UniCredit, Anthem, and Verizon made headlines in just a four week period this year. Phishing, disgruntled employees, ransomware, zero days, and human error are costing companies billions.
With seemingly infinite threats and limited resources, how do you know what to prepare for? It would be great if an IT manager could simply declare, “The biggest cyber threat is the MacGuffin virus. But our network will be completely safe forever if we just buy this security thingamajig.” Unfortunately, risk management requires a bit more nuance and cognitive effort. Declaring any one thing to be “the biggest threat” is misleading. Each organization has unique goals, information assets, and risk appetite. A small threat to one company may be the biggest threat to you. It is also a poor approach in the long term. Constantly posturing for threats found in headlines and chasing the latest dragon to slay will lead to fatigue and a myopic view of the threat landscape.
Developing an evidence-based understanding of the hazards to your network is a practical approach to building a defense. This is a continuous process of prioritizing and discovery. This article will provide some fundamental tools for practicing good cyber threat intelligence.
Identify Threats Using Threat Categories
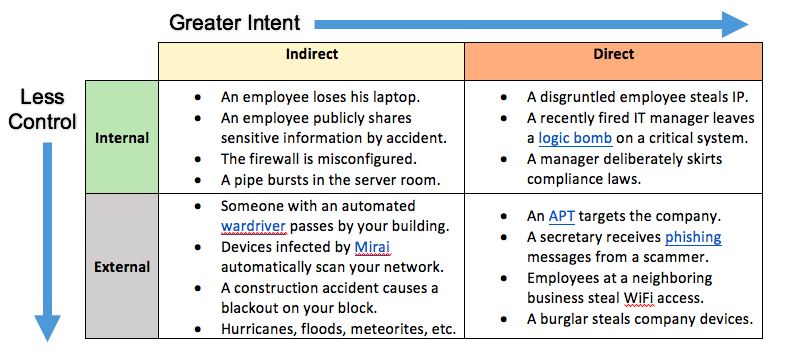
Threats to your network will fall into a matrix of four categories: indirect or direct, and internal or external. (You can find a chart with examples at the end of this article.) An indirect threat is something that poses an unintended risk to your organization. This includes accidents like employees losing cell phones and ID cards. This would also cover indiscriminate campaigns that affect many hundreds of thousands of users, as they are not directly targeting any one group or individual. Natural events like hurricanes and floods are also considered indirect threats. Direct threats are targeted and deliberate attacks on your network. A human actor is responsible in every instance. Criminal hackers who target your network for financial gain are one example of a direct threat.
Internal threats exist inside the organization. These are things your organization has control over. Disgruntled and careless employees are obvious internal threats. Less obvious internal threats are poorly configured devices and physical safety hazards. External threats exist outside the network and the control of the network’s owners. This includes people outside the organization, like guests and customers. It also includes things, like neighboring structures and foreign governments.
Generally speaking, the direct external threat is going to pose the greatest risk to your organization. While direct internal threats can be dangerous, they are often most effective in their criminal activity when working in concert with an external party. Internal threats are also subject to greater monitoring than external ones. Presumably, your network administrators can monitor your employees’ internet browsing habits, and hopefully abnormal behavior would stand out. You can intervene before the situation worsens. However, the external threat is an unknown. You do not know who the external threat actors are, so you cannot monitor them. You do not know their capabilities, so it is difficult to evaluate the potential damage they could cause. By the time you have learned the attacker’s target and motive, you may already be under attack.
But just because external threats are unknown does not mean you cannot prepare for them. Direct threats are either opportunistic or persistent. Both opportunistic and persistent threats are human attackers who want to cause you deliberate harm. Their only true distinction is how they choose and pursue targets. An opportunistic attacker searches for weakly defended and unsecured systems without discrimination, taking anything valuable inside. If a target proves too difficult and time consuming, or if he finds nothing of value, he moves onto a new target. Opportunistic hackers are comparable to burglars who look for the first unoccupied house with doors left unlocked, then look for anything valuable inside. Most hackers are opportunistic crooks and pick their targets based solely on their vulnerability. Conversely, a persistent attacker will usually have a specific target and a well-defined objective. The key difference is that a persistent attacker will not cease in his attempts until either he succeeds or is apprehended. Where the opportunistic hacker is like a house burglar, the persistent hacker is more akin to a hitman who will pursue a target relentlessly.
Mapping Defense to the Threat
We could make these categories even more granular, but this is probably far enough at this stage. Here is an exercise: List the information technology assets your organization uses—sensitive documents, software, hardware, communication media, etc. Go down the list and ask the following questions:
- Who is responsible for this asset?
- What is the value of this asset to the organization?
- If this asset is lost, destroyed, stolen, or made unavailable, what would be the impact to the organization? What would it cost to replace?
- What could accidentally happen to this asset? Is there anything that can be done internally to prevent or mitigate that risk?
- If an employee misused or abused this asset, how would anyone know?
- What was the impact on operations last time a natural disaster hit this local area? How were neighboring businesses affected?
- What sort of cybercrime have other similar organizations had to deal with in the last two years? Are our employees aware of the risks?
- Are there any indicators of compromise (IoC) on our network that suggest an intrusion has already happened?
Clearly, this is not an exhaustive inquiry, but it should spark a discussion on what risks your organization faces. It also may start to reveal areas where your organization could be unprepared, and taking steps to improve cybersecurity posture is better done now than later. Improvising defenses during a crisis is definitely a bad idea, so invest some time today to research the threat landscape.
Author: Louis Papa
Silent Storm Security Contributor | Security Engineer